Web Server Settings
The Web Server page is for configuring the HTTP and HTTPS ports, enabling SSL/TLS, redirecting traffic through a known address, and specifying whether or not all HTTP traffic should be forcefully redirecting to HTTPS.
If you are allowing users to access your Gateway from outside your network (through the Internet), you will need to configure the Public HTTP Address settings.
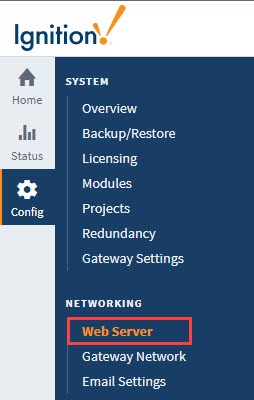
SSL/TLS Settings
On the Web Server screen you can view details of an SSL certificate details, export keys, remove the installed SSL certificate, and transition to a CA signed certificate.
From the Gateway Webpage, click on Config > Networking > Web Server. From the Web Server page, click on the View Details button. See Adding a Signed Security Certificate process for more information on enabling SSL/TLS and installing security certificates.
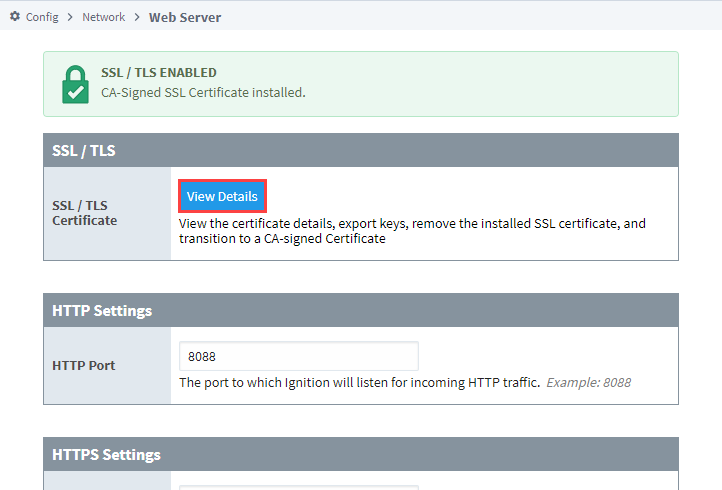
On the Certificate Details page, you can also generate a Certificate Signing Request (CSR) by clicking the Generate CSR button in the upper right.
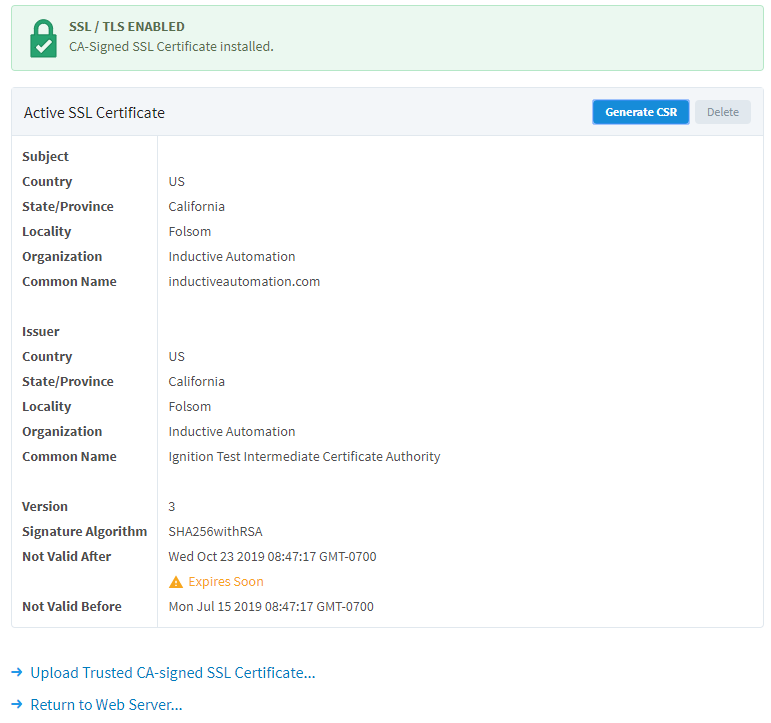
Clicking on Upload Trusted CA-signed SSL Certificate... will open the Certificate Wizard. This will allow you to update your SSL/TLS configuration by uploading a second certifcate that replaces the original.
Clicking on Return to Web Server... will take you back to the main Web Server Settings page.
For more information, see Secure Communication (SSL/TLS).
HTTP and HTTPS Settings
HTTP Settings
| Property | Description |
|---|---|
| HTTP Port | The port Ignition will listen for incoming HTTP traffic, for example: 8088. |
| Use Proxy Forwarded Headers | New in 8.1.10 When enabled, the Gateway inspects each incoming HTTP request in search for headers that indicate it has been forwarded by one or more proxies. If these headers are present, then the request is updated so that the proxy is not seen as the other end point of the connection from which the request originated. CAUTION: Enabling this setting when users can directly connect to the Gateway is a security risk. This setting is intended to be used in scenarios where untrusted users will not be able to bypass a trusted proxy that is responsible for setting the appropriate headers. For more information, see Use Proxy Forwarded Headers Explained. |
| Resolve Client Hostnames | New in 8.1.10 When enabled, Ignition's web server will attempt to resolve the remote HTTP client's hostname by performing a reverse DNS lookup using the remote HTTP client's IP address where appropriate. Enabling this setting could have a performance impact as the Gateway may attempt an expensive hostname lookup when handling requests. When disabled, Ignition's web server will not attempt to resolve hostnames and any queries for the remote HTTP client's hostname will result in their IP address instead. When enabling this setting, it is highly recommended that reverse DNS is configured to prevent host lookup failures. This includes configuring valid mappings from user IP addresses to their hostnames, and from user hostnames back to their IP addresses. If reverse DNS isn't configured, then DNS queries could block certain requests until the queries time out (default of 10 seconds). |
HTTPS Settings
| Property | Description |
|---|---|
| HTTPS Port | The port Ignition will listen for incoming HTTPS traffic, for example: 8043. |
| Force Secure Redirect | When enabled, and if SSL / TLS is enabled, all http traffic will be redirected to its https counterpart. Disabled by default. |
| Included Cipher Suites | Whitelist of included cipher suites for clients connecting to Ignition using SSL/TLS. |
| Excluded Cipher Suites | Blacklist of excluded cipher suites for clients connecting to Ignition using SSL/TLS. Takes precedence over allowed cipher suites. Note: The Excluded and Included Cipher Suites settings only apply to the port specified in the HTTPS Port field. If you need to Whitelist or Blacklist cipher suites for port 8060, refer to the Gateway Network > HTTPS Settings information on the Gateway Configuration File Reference page. |
HTTP and HTTPS Connectors Restart
Certain actions will cause the HTTP port and/or the HTTPS port to restart. Refer to the following table for details.
| Configuration Change | HTTP Port Restarted? | HTTPS Port Restarted? |
|---|---|---|
| HTTP Port | Yes | Yes |
| HTTPS Port | Yes | Yes |
| Force Secure Redirect | No | Yes |
| User Included Cipher Suites | No | Yes |
| User Excluded Cipher Suites | No | Yes |
| SSL/TLS Setup | No | Yes |
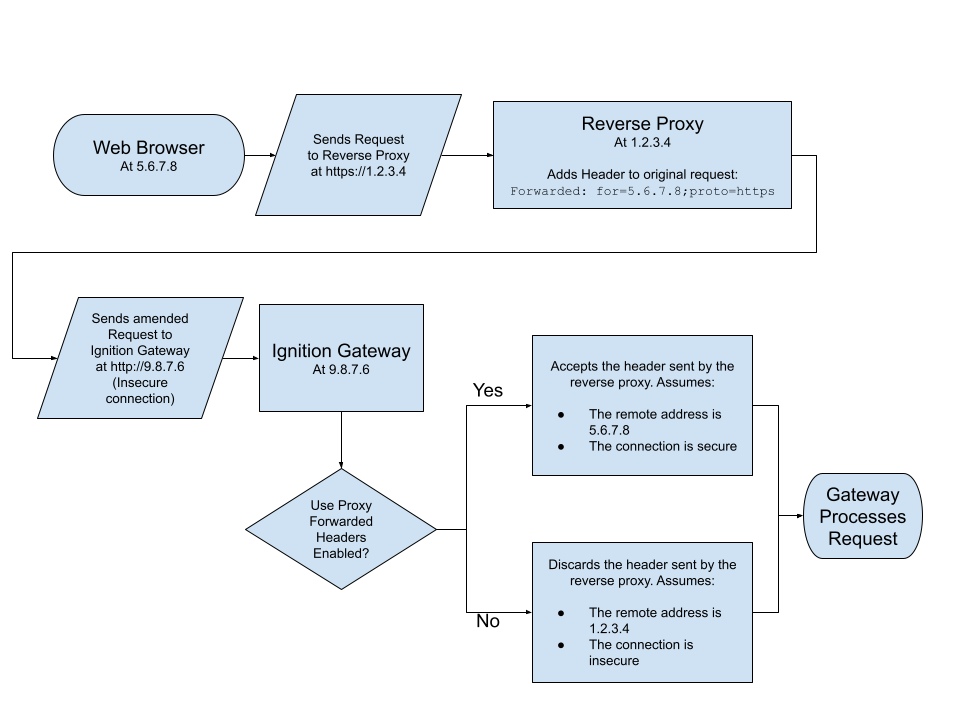
Use Proxy Forwarded Headers Explained
While enabled, the Gateway's web server will look for request headers mentioned on this page: ForwardRequestCustomizer. Depending on what headers come in, the web server will alter its view of the remote client's connection on the incoming http request. The following is a list of which parts of the request that can be altered, although it's not exhaustive:
- The remote HTTP client's IP address
- The remote HTTP client's port
- The scheme used by the remote HTTP client when connected to the Gateway through one or more proxies (i.e., http/https)
- Whether or not the connection is considered secure
- The host/IP and port that the remote HTTP client used to connect to the Gateway through one or more proxies
While this setting is enabled, if the Gateway does not see any of the mentioned headers, then the request will not be altered, effectively acting as if the setting is disabled.
The diagram below represents a request originating from a browser, and demonstrates how this setting can impact the request.
Public HTTP Address
If you are allowing users to access your Gateway from outside your network (through the Internet), you will need to configure the Public HTTP Address settings.
Public HTTPS Address Settings
| Property | Description |
|---|---|
| Auto Detect HTTP Address | To specify an explicit HTTP address that Vision Clients and Perspective Sessions will use, turn this off. Most users will leave autodetect on. Enabled by default. |
| Public Address | The public facing address that Vision Clients and Perspective Sessions must use to connect. If Force Secure Redirect is enabled, redirected connections will use this address, for example: yourcompany.com. |
| Public HTTP Port | The public facing HTTP port that Vision Clients and Perspective Sessions must use to connect, for example: 80. |
| Public HTTPS Port | The public facing HTTPS port that Vision Clients and Perspective Sessions must use to connect. If Force Secure Redirect is enabled, redirected connections will use this port, for example: 443 |
Cipher Support
Listed below are the supported cipher suites for both 8043 and 8060 TLS ports.
Cipher suites enabled by default:
TLS_AES_128_GCM_SHA256
TLS_AES_256_GCM_SHA384
TLS_CHACHA20_POLY1305_SHA256
TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_CHACHA20_POLY1305_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
TLS_EMPTY_RENEGOTIATION_INFO_SCSV
Cipher suites disabled by default:
TLS_DHE_DSS_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_256_CBC_SHA
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384